Hyperledger Hackfest, Amsterdam: Hyperledger Fabric and Indy
4 min recap, Hyperledger Hackfest event. You can find the related video below.
We continue the our Hyperledger adventure in Amsterdam Hyperledger Hackfest.

Hyperledger Fabric: Updates and News
Project supported by IBM team, which has been the come a long way by Hyperledger formation so far, “Hyperledger Fabric” the updates are continuing at the full speed. The 1.2 version of the project was published in the near future, the road map is more or less obvious.
Chris Ferris, head of the IBM Blockchain Team, delivered the developments in Fabric to us.
Let us briefly convey the innovations that draw our attention.

Ethereum Virtual Machine Chaincode
The most important feature that comes with Fabric 1.2, Ability to run EVM chaincodes on Fabric. This is also a very important step for the Ethereum technology, one of the most effective solutions in the world of Blockchain, to meet with the Hyperledger Fabric project. The structures on which we can run EVM chain codes on the fabric will provide us with considerable flexibility and new functions. We expect to be able to use the EVM chaincode in a fully stabilized version of the 1.3 Fabric which is expected to be released soon, although this is still in trial phase in version 1.2.
Pluggable Endorsement Policy + Validation
While the Hyperledger Fabric project was on it’s way, the most important difference from the other solutions was the changeable Consensus (Ordering) service and the MSP (Membership Service Provider) structure that could be varied according to the needs, They also have a Pluggable Endorsement Policy + Validation (Administration and Validation) process now. In the near future, we were able to test in version 1.1, and in SideDB, It is more powerful and stable in this version.
In version 1.3 and 1.4 of Hyperledger Fabric which will be released after version 1.2, we will start to use radical changes and new consensus mechanisms.
Zero Knowledge Asset Transfer (ZKAT)
ZKP (Zero Knowledge Proof) algorithm which is widely spoken in the world of Blockchain, which will come out with 1.3 version.
“How can I prove to myself that I have a knowledge, without giving it to the other side?” Zero Knowledge Proof (ZKP)
In the Hyperledger Fabric solution, the main components that make Transactions Private are “Channels” and “Custom Transactions”. In addition, the ZKP (Zero Knowledge Proofs) algorithm produces the same probing solution.
Hyperledger Fabric focuses on two main solutions when using ZKP capability.
- Anonymous client authentication with Identity Mixer
- Protection of Private Asset Transfer (Private-Preserves of Exchange Assets)
We will have these features with version 1.3.
For details :Private and confidential transactions with Hyperledger Fabric
Java Chaincode
We can use the Go language or chain codes written in NodeJS in the current version of the Hyperledger Fabric. We build our smart contracts using one of these languages, and we manage our processes through them. One of the major innovations with version 1.3 is the Java Chaincode option. This is an important step that will allow many Java programmers to join the Blockchain ecosystem with Java, a very powerful language that has long been expected by many programmers.
So when Hyperledger Fabric 1.3 comes out, we will be able to run chaincode on the Fabric network in the following languages.
- GO Language
- Node JS
- Solidity (Ethereum Virtual Machine Chaincode)
- Java
RAFT Consensus Mechanism
One of the most important innovations coming with version 1.3 is the RAFT Consensus Structure, which does not include the Byzantine Error Tolerance previously used by JpMorgan’s Quorum solution and has similar features to the Crash Fault Tolerance (Kafka) structure can now be used and preferred in the Orderer Service in Hyperledger Fabric.
For details : RAFT
In addition to these, web3 proxy and new composer functions will come with version 1.3.
PBFT Consensus Mechanism
At last, The PBFT Consensus Mechanism, which will include the Byzantine Fault Tolerance, which is one of the most important developments in the Hyperledger Fabric project, which will bring the Hyperledger Fabric rise to top, will be included with the Orderer Service in the 1.4 version.
For details : PBFT and Byzantine Fault-Tolerance
The release date for 1.4 is January 2019, announced by Chris Ferris, head of the IBM Blockchain team.
Hyperledger Indy: Sovrin SSI
I want to give basic information about Indy, before I start the article.
Indy was developed as Sovrinbefore joining the Hyperledger Projects. (Sovrin continues to develop outside of Indy at the same time.)
What is it, Sovrin?
The Sovrin Foundationis an international, non-profit-making organization established to manage the world’s first “Self-Soverign Identity” (SSI) network.
Sovrin is an open source identity network based on “Distributed Ledger Technology”. The usage is open and permissible. Anyone can use it. Can participate.
Earlier in May 2017, Sovrin announced that he joined the Hyperledger Projects with the Indy name. This project is expected to provide unparalleled confidence in the Blockchain Distributed Ledger system.
It is important not to forget that Hyperledger Indy works with a completely Sovrin infrastructure and is the same. At the same time, the Sovrin Foundation continues to develop and operate the Sovrin Network, which is managed by the Sovrin Trust Framework.
Hyperledger Hackfest In Amsterdam a comprehensive chapter for the Hyperledger Indy was reserved. Nathan George, CTO of Sovrin Foundation, started by conveying theoretical information about the Indy Project. He then exemplified it with an application.

Let’s remember the basic purpose of the Indy project.
Hyperledger Indy is a distributed ledger, purpose-built for decentralized digital identity. It provides tools, libraries, and reusable components for creating and using independent digital identities rooted on blockchains or other distributed ledgers so that they are interoperable across administrative domains, applications, and any other “silo.” Administrative areas can work with applications. Thus, it has a power that can be easily added to many areas. For example; It is expected to be used in many areas such as government agencies, health institutions, educational institutions, insurance systems.
To sum up, Indy is a safe system where you can safely share your digital identity with those who need it.
Transformations of Digital Identities
The Internet is a communication network with its own standards, in which many computer systems are interconnected. Computer systems send and receive data packets to each other. Communication is always done in this way. We can say that the Internet was built around machines, not people.
There was no way in the early days of the Internet to keep track of who was connected. In fact this was a good situation in terms of security. We use e-mail to send a message, we use www to receive a data package. But as applications became more complex with Web 2.0 later on, e-commerce and social platforms became widespread. The identity question has become more important.
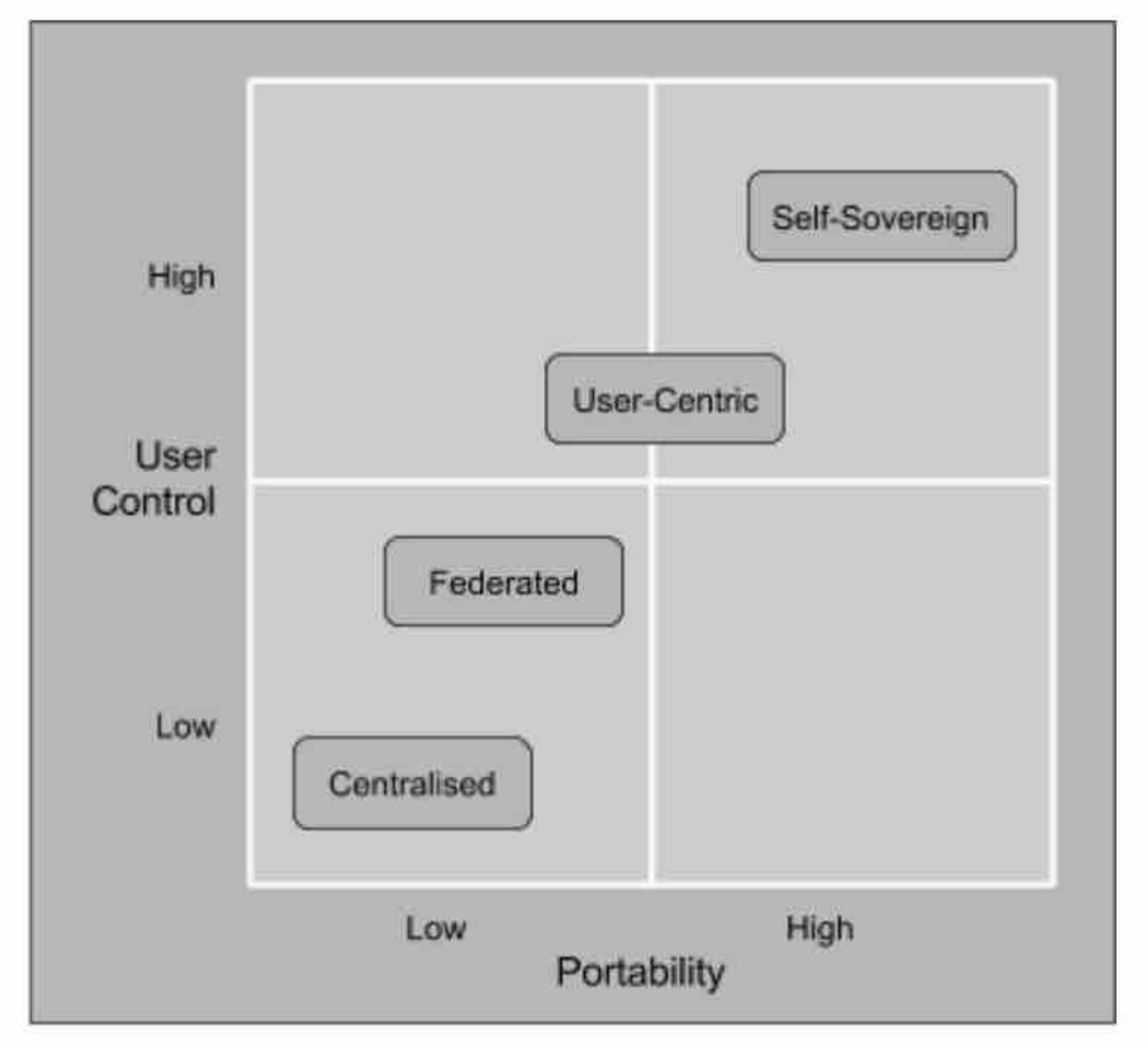
Centralized Identity :
Though the early days of the Internet focused on building a network which would decentralize the world, this decentralized network ultimately operated on a base layer of centralized identities. Centralized organizations like IANA (1988) determined the validity of IP addresses, and ICANN (1998) arbitrated domain names. Eventually, trust became an issue on both sides of e-commerce.
“Can I trust my customer to pay their bills?”
“Can I trust the service provider to deliver my goods?”
The centralization of the digital identity has made it possible to give these data to the central authorities, not to the users whose identities should belong. it is still the center of most Internet identities today. It is owned and controlled by a single entity, such as an e-commerce site or social network. A central identity can work within its own domain, but struggles to keep up with the rapid growth and diversity of online websites and services that users interact with. For this reason, a data chaos comes into play.
Data Chaos
- Your identity and other personal data have spread throughout the Web.
- Users must manage hundred of username and their passwords.
Data Slavery
Our digital identities are belong to the certification authorities, domain name registrars and individual platforms. We do not actually have our own data, and we can say that we can not manage them, although we can manage them. For example; Facebook, Google, your bank, your university)

#1 Centralized Identity
Federated Identity :
If we summarize briefly, a federated structure makes it possible for one user to log into a service using the credentials of another. It will provide a degree of data move ability to a central identity.

#2 Third Party IDP (Federated) Identity
User-Centric Identity
The user fills in his data repository with the information. This information is then given to other organizations with the permission of the individual and a record of these provisions is kept.
Self-Soverign Identity (SSI)
“SSI is a digital identity that an individual or organization has 100% ownership and control. No one else can read it, use it, turn it off, or see it without the owner’s explicit consent. This simple form of identity is personality. It’s extremely safe and goes to where you went.”
SSI offers solutions to enable people and businesses to store their own credentials on their own devices and share it effectively with organizations that require authentication without relying on a central pool of credentials.

Nathan, shared developments about the Indy SDK. How to install SDK, how to run cli-tool, how to start local nodes.
All of this information is detailed in the indy project on github. If you are interested in Hyperledger Indy, I suggest you review the SDK.


At the other hand, there is a separated section for Amsterdam Event of Hyperledger. Please check this URL. At the end of the article, I will share an example of Nathan’s application.

You can see the demo below.
Sources
1- HyperledgerHackfest Amsterdam Notları, DLK Archive
